After listening the word Hacking will all have common question in mind that-
How to hack my boy/girl friend facebook/instagram account ?
In now a days- How to hack PUBG ?
So,Please don't use the below information for illegal works.
There are mainly 2 types of hackers -
How to hack my boy/girl friend facebook/instagram account ?
In now a days- How to hack PUBG ?
So,Please don't use the below information for illegal works.
There are mainly 2 types of hackers -
- Black hat hackers - Those who hack information illegally for their gain. Black hat hackers break into secure networks to destroy, modify, or steal data, or to make the networks unusable for authorized network users. They are cyber criminals.

- White hat hackers - They are ethical hackers and security experts. They help peoples who falls in black hat hackers trap. They works as cyber security.
Some commonly hacking attacks that all should aware of -
- Brute Force Attack - A brute force attack is a trial and error method used by application programs to decode encrypted data such as passwords.
Hackers try different combinations again and again to find the correct password.
For example : If hackers finds that your password is a phone number of 10 digits then he/she will try to enter all possible combinations. i.e (0000000000, 0000000001, 000000002, 0000000003, ........,9999999997, 9999999998, 9999999999).
So, total combinations will be 1010 . So, he/she had to try at most 1010 times.
A normal person cannot try that many combinations. So, they write a loop program using programming languages. So, computer performs this task.
- Dictionary Attack - This is quite much same as brute force attack but it try frequently used password combinations to crack password.
Like - They have file where frequently used passwords are stored. So, they bring that file in their program and loops through it(i.e try all combinations) and check whether any password matches or not.
- Phishing Attack - Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers.
For example - You open any non-trusted site and clicks on sign in with facebook option showing there.So, when you click that link facebook page will appear but it may not be facebook page i.e. only front-end design of page will look like facebook but when you add your information (i.e email and password) request will not go to facebook server/database.
Because it's not facebook database it's hacker database in which they make front-end design same but back-end is connected to their server.
So, First check the url of the page i.e(www.facebook.com) is there on top or not.
So, Be Alert !!!
This was only facebook example but there are also sites in which people even give their credit card details on such fake pages.

- Keyloggers - A keylogger is a technology that tracks and records consecutive key strokes on a keyboard. Because sensitive information such as usernames and passwords are often entered on a keyboard, a keylogger can be a very dangerous technology.Keyloggers are often part of malware, spyware or an external virus that enters in our computer as useful program and sends our information to hackers.
You can easily download it from internet.
For example - If your friend asks that he/she want to open his/her facebook account from your device. And then you secretly opens keylogger in background (this program will be hidden and can't be easily detected). So what your friend types from your keyboard will be saved on your device. And you can easily get his/her email/password.
So, friends don't use it for illegal works.
Many parents use it for their child to get information of their child (i.e what they are typing and seeing 😁😁 ).
Yes, it also a program written in programming languages like-python,c,c++,java etc.

- SQL injection attack- An SQL injection is a computer attack in which malicious code is embedded in a poorly-designed application and then passed to the backend database. The malicious data then produces database query results or actions that should never have been executed.This attack is used to steal the information of users from remote database.
For ex-
You visit any weak security website made in PHP-Mysql. There is login form. So, what happens when you add you email,password is that, data will go to backend and check that user exist in it's record or not.
So, the query for that is -
“SELECT * FROM users WHERE account = ‘“ + userProvidedAccountDetails +”’;”
Above query will run for the same.
But, if you write '' or '1'='1 in place of email/password then query will become -
“SELECT * FROM users WHERE account = ‘’ or ‘1’ = ‘1’;”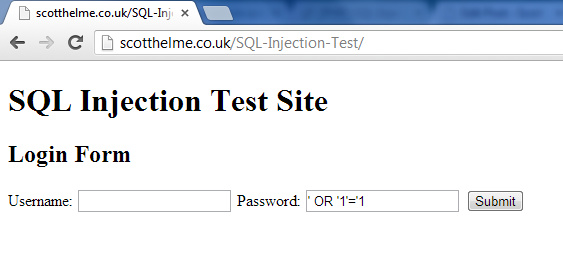
Note that here OR operator is used which means either one statement will correct so we know 1=1 hence, it will always be true so database will give the information of all users in it.
By using the queries you can edit or even delete the database.
So, be aware of these attacks.
And and don't use them to hack someone's information as it is cyber crime and if you are caught strict actions will be taken and punishment will be given for the same.
There are also many attacks that I have not mentioned here.
So, Feel free to ask any doubt.






0 Comments